Hola, comunidad:
Mientras escribía un artículo ayer, me di cuenta de que estaba tan ocupada con las personas que se acercaron a la mesa de la Developer Community en el Tech Exchange que se me olvidó sacar fotos para vosotros. Por suerte, me di cuenta de mi error y lo corregí 😉.
Así que, ¡veamos qué ocurrió el martes en el InterSystems Ready 2025! Comenzó con un discurso de Scott Gnau sobre el enfoque y la arquitectura de la plataforma de datos de InterSystems, y cómo se diferencia de todos los demás sistemas de gestión de bases de datos (DBMS).

Después, @Tom Woodfin y Peter Lesperance se adentraron en los detalles del uso de las novedades de IRIS en Epic:

Luego, @Gokhan Uluderya habló sobre los datos en la IA y la importancia de contar con datos de calidad para poder aplicar GenAI o Búsqueda Vectorial sobre ellos:
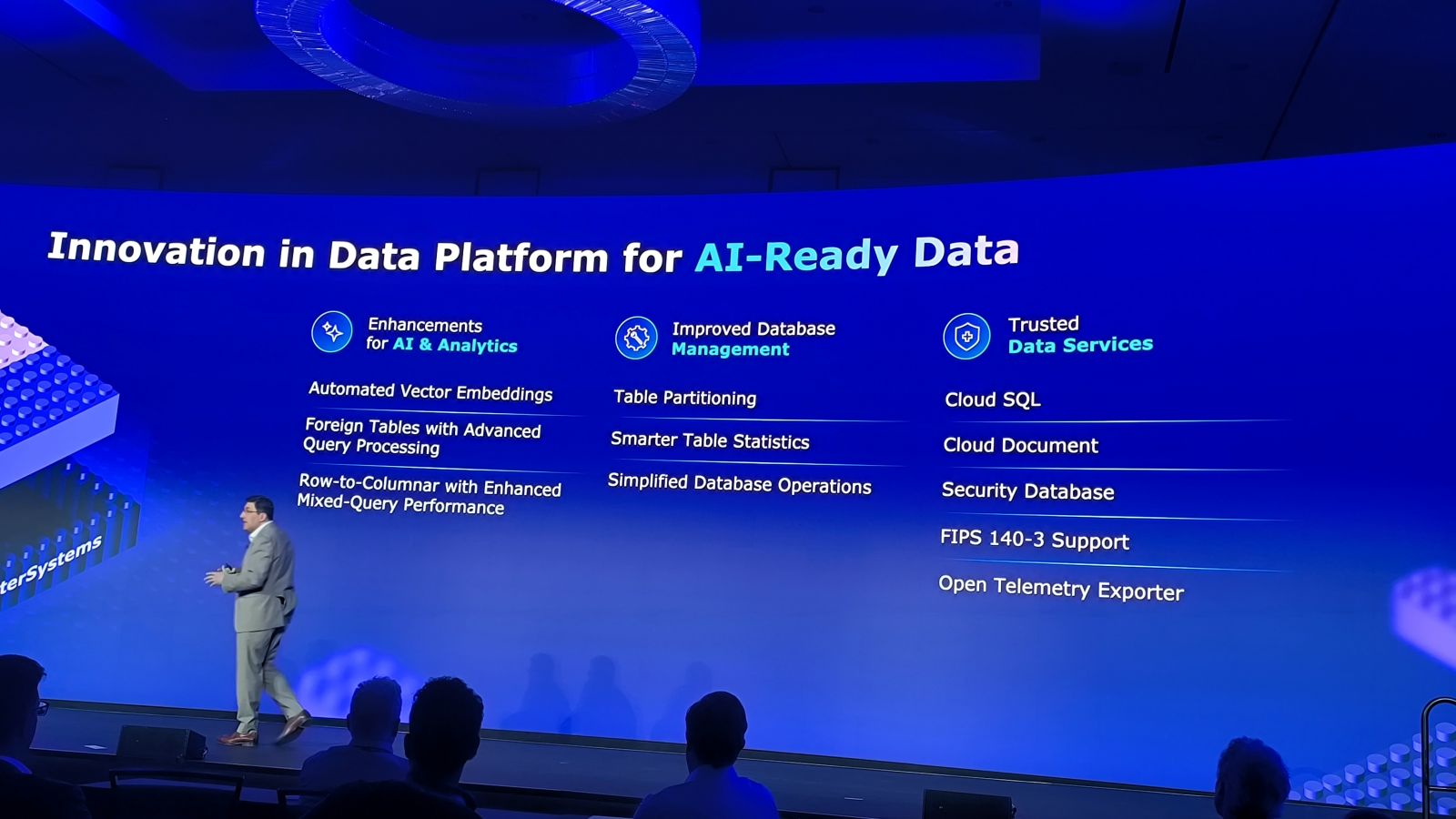
@Jeff Fried retomó este tema y profundizó más en la estrategia de InterSystems GenAI:
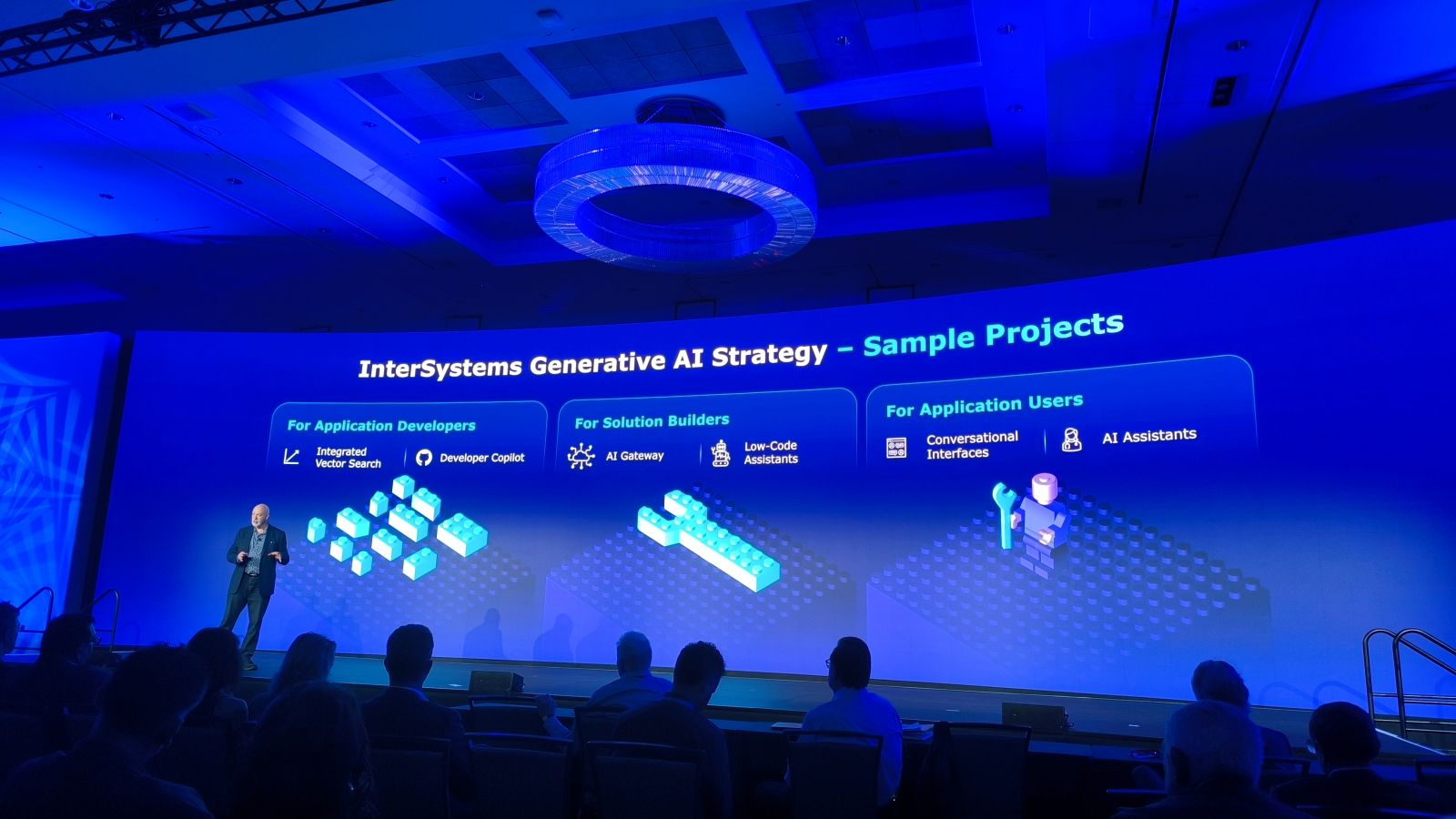
Daniel Franko resumió las herramientas disponibles para los desarrolladores de IRIS for Health:

Después de la comida, la mayoría de los participantes continuaron con las sesiones o el Tech Exchange. Por ejemplo, @Raj Singh pasó por nuestra mesa y hablamos sobre el actual Concurso de Ideas.

@Henrique Dias, @Henry Pereira y @Dean Andrews también se acercaron al stand:

@Lorenzo Scalese, @Dean Andrews , @Derek Gervais
.jpg)
@Sergei Shutov, @Anastasia Dyubaylo, @Vishal Pallerla

@Iryna Mykhailova, @Anastasia Dyubaylo, @Bob Kuszewski

@Henrique Dias, @Benjamin De Boe, @Anastasia Dyubaylo, @Enrico Parisi, @Henry Pereira, @Iryna Mykhailova, @José Pereira

Los "Mosqueteros" (@Henry Pereira, @Henrique Dias, @José Pereira) con @Anastasia Dyubaylo
.png)
@Dean Andrews, Mariam Makhmutova, @Anastasia Dyubaylo, @Derek Gervais
.png)
@Muhammad Waseem, @Guillaume Rongier, @Anastasia Dyubaylo, @Oliver Wilms
.png)
@Derek Gervais, @Anastasia Dyubaylo, @Ben Spead, @Thomas Dyar
.png)
Este año, para hacerlo más interesante, preparamos un desafío especial para nuestros invitados desarrolladores: ¡un quiz de Global Masters!
Aquí están @Derek Robinson, @Myles Collins y @Patrick Sulin intentando acertar las 5 respuestas correctamente:

En el próximo artículo, ¡descubriréis quién superó el desafío!
Mientras todo esto ocurría en la mesa de la Developer Community, en la pantalla grande del Tech Exchange había presentaciones, como la de @Brett Saviano sobre VS Code:

Y presentaciones en mesas más pequeñas, por ejemplo, la de @Guillaume Rongier:
.png)
Fuera del Tech Exchange, las startups estaban haciendo sus presentaciones. Por ejemplo, SerenityGPT, que creó nuestro maravilloso DC AI Bot y DC AI Chat:
.png)
Y por la noche fuimos a Universal City Walk y disfrutamos del concierto de Integrity Check, ¡que fue espectacular!

Después del concierto, tuvimos el placer de la compañía del guitarrista, también conocido como @Randy Pallotta.

Pasamos un rato maravilloso en Universal, que fue un gran cierre para un día estupendo.


.png)